Review of Last Year’s Predictions
Increase in Services Offering AV Evasion for Malware (Cryptors)
We continuously monitor underground markets for the emergence of new “cryptors,” which are tools specifically designed to obfuscate the code within malware samples. The primary purpose of these tools is to render the code undetectable by security software. In 2024, our expert observations indicate that commercial advertising for these cryptors have indeed gained momentum. Cryptor developers are introducing novel techniques to evade detection by security solutions, incorporating these advances into their malware offerings.
Pricing for these tools has remained consistent, ranging from $100 for a monthly subscription to cryptors available on dark web forums to as much as $20,000 for premium private subscriptions. There has been a shift toward the development and distribution of premium private solutions, which are becoming increasingly prevalent compared to public offerings.
Verdict: prediction fulfilled 
Evolution of “Loader” Malware Services
As anticipated, the supply for the “loader” malware family has been constant in 2024. These loaders exhibit a wide range of capabilities, from mass-distributed loaders available at low prices to highly specialized loaders tailored to detailed specifications with prices reaching into the thousands of dollars.

Examples of loader offers
Additionally, threat actors appear to be increasingly using multiple programming languages. For example, the client component of the malware may be developed in C++, while the server-side admin panel is implemented in Go.
Along with the wide variety of loader offerings, we have also seen demands for specific functionality tailored to launch a particular infection chain.

Example of searching for a loader with specific requirements
Verdict: prediction fulfilled 
Growth of Crypto Asset Draining Services on Dark Web Markets
In 2024, we observed a surge in the activity of “drainers” across dark markets. These are malicious tools designed to steal the victim’s crypto assets, such as tokens or NFTs. New drainers emerged throughout the year and were actively promoted on various dark web platforms. In general, the number of unique threads discussing drainers on underground markets increased from 55 in 2022 to 129 in 2024, which is remarkable. At the same time, these posts frequently served as redirects to Telegram.
The number of unique threads about drainers on the dark web (download)
In fact, in 2024, Telegram channels were a prominent hub for drainer-related activity.

Dark web post containing links directing potential collaborators to Telegram
Drainer developers are increasingly focused on serving their long-term clients, with most activity now conducted in invite-only channels.
In terms of functionality, drainers have remained largely consistent, with a continued emphasis on incorporating support for new crypto-related assets such as emerging coins, tokens, and NFTs. 2024 also saw the discovery of the first mobile drainer.
Verdict: prediction fulfilled 
Popularity of Black Traffic Schemes on Underground Markets
In 2024, the popularity of black traffic schemes on underground markets remained constant. Black traffic dealers have maintained their operations by promoting malicious landing pages through deceptive ads. Sales activities for these services remain robust on underground markets, with demand holding steady, further highlighting the effectiveness of mainstream ad delivery platforms for malware distribution. This method continues to be a popular choice for cybercriminals looking to reach a wider audience, posing an ongoing threat to online users.
Verdict: Partially fulfilled
Market Dynamics of Bitcoin Mixers and Cleaning Services
In 2024, there was no significant increase in the number of services advertising cryptocurrency “cleaning” solutions. The majority of established and popular services have maintained their presence in the market, with little change in the competitive landscape.
Verdict: prediction not fulfilled 
Our Predictions for 2025
Data Breaches Through Contractors
When abusing company-contractor relationships (trusted relationship attacks), threat actors first infiltrate a supplier’s systems and then gain access to the target organization’s infrastructure or data. In some cases, these attacks result in significant data breaches, such as the case where attackers allegedly accessed Ticketmaster’s Snowflake cloud account by breaching a third-party contractor. Another prominent threat actor employing this tactic was IntelBroker – the actor and their associated gang reportedly breached companies like Nokia, Ford, a number of Cisco customers including Microsoft, and others through third parties.

Profile of the actor named IntelBroker on a popular dark web forum
We expect to see the number of attacks through contractors leading to data breaches at major end targets to continue to grow in 2025. Cloud platforms and IT services often store and process corporate data from multiple organizations, so a breach at just one company can open the door to many others. It is worth noting that a breach does not necessarily have to affect critical assets to be destructive. Not every data breach advertisement on the dark web is the result of a genuinely serious incident. Some “offers” may simply be well-marketed material; for example, certain databases may combine publicly available or previously leaked data and present it as breaking news, or simply claim to be a breach for a well-known brand. By creating hype around what is actually old – and probably irrelevant – data, cybercriminals can provoke publicity, generate buzz, and damage the reputation of both the supplier and its customers.

IntelBroker’s dark web post claiming a Tesla data breach, later edited to claim to be a breach of a third-party EV charging firm
In general, we have noticed an overall increase in the frequency of corporate database advertisements on the dark web. For example, on one popular forum, the corresponding number of posts in August-November 2024 increased by 40% in comparison with the same period last year, and peaked several times.
Number of dark web posts distributing databases on one popular forum, August 2023-November 2024 (download)
While some of this growth may be attributed to the reposting or combining of older leaks, cybercriminals are clearly interested in distributing leaked data – whether new, old, or even fake. Consequently, in 2025, we are likely to witness not only a rise in company data hacks and leaks through contractors, but also an overall increase in data breaches.
Migration of Criminal Activity from Telegram to Dark Web Forums
Despite a spike in cybercriminal activity on Telegram in 2024, we expect the shadow community to migrate back to dark web forums. Shadow Telegram channels are increasingly being banned, as noted by their administrators:

Examples of messages from threat actors announcing a ban on their Telegram channels and accounts
The return or influx of cybercriminals to dark web forums is expected to intensify competition among these resources. To stand out and attract new audiences, forum operators are likely to start introducing new features and improving conditions for data trading. These may include automated escrow services, streamlined dispute resolution processes, and improved security and anonymity measures.
Increase in High-Profile Law Enforcement Operations Against Cybercrime Groups
2024 was a significant year in the global high-profile fight against cybercrime. The world has seen many successful operations – Cronos against LockBit, the takedown of BreachForums, the arrest of WWH Club members, successful initiatives like Magnus against RedLine and Meta stealers, and Endgame against TrickBot, IcedID, and SmokeLoader, and more. We at Kaspersky also actively contributed to law enforcement efforts to combat cybercrime. For example, we supported INTERPOL-coordinated action to disrupt the Grandoreiro malware operation, helped counter cybercrime during the 2024 Olympics, and contributed to Operation Synergia II, which aimed to disrupt cyberthreats such as targeted phishing, ransomware, and infostealers. We also assisted the joint INTERPOL and AFRIPOL operation combating cybercrime across Africa. These and many other cases highlighted the coordination and collaboration between law enforcement and cybersecurity organizations.
We expect 2025 to bring an increase in arrests and takedowns of high-profile cybercriminal group infrastructures and forums. However, in response to the successful operations of 2024, threat actors will likely switch tactics and retreat to deeper, more anonymous layers of the dark web. We also expect to see the emergence of closed forums and an increase in invitation-only access models.
Rise of Stealers and Drainers as Services on the Dark Web
Cryptocurrencies have been a prime target for cybercriminals for years. They lure crypto users to scam sites and Telegram bots under various guises, and add crypto-stealing functionality to infostealers and banking Trojans. With the price of Bitcoin setting record after record, the popularity of drainers specifically designed to steal cryptocurrency tokens from victims’ wallets is likely to persist in the coming year.
Infostealers are another type of malware that harvests sensitive information from users’ devices, including private keys for cryptocurrency wallets, passwords, browser cookies, and autofill data. In recent years, we have witnessed a dramatic rise in credential leaks driven by this malware, and we expect this trend to continue – and in some sense evolve. Most likely, we will see the emergence of new families of stealers, along with an increase in the activity of those that already exist.
Both stealers and drainers are likely to be increasingly promoted as services on the dark web. Malware-as-a-Service (MaaS) – or “subscription” – is a dark web business model that involves leasing software to carry out cyberattacks. Typically, clients of such services are offered a personal account through which they can control the attack, as well as technical support. It lowers the initial threshold of expertise required by would-be cybercriminals.

Example of a stealer offered through the MaaS model
In addition to publications on the dark web featuring stealers or drainers themselves, we also see posts looking for traffers – people who help cybercriminals distribute and promote stealers, drainers, or scam and phishing pages.

Examples of traffer searches for drainers

Example of a traffer search for a cryptoscam (not a drainer)
Fragmentation of Ransomware Groups
Next year, we may see ransomware groups fragmenting into smaller independent entities, making them more difficult to track and allowing cybercriminals to operate with greater flexibility while staying under the radar. Kaspersky Digital Footprint Intelligence data shows that in 2024 the number of Dedicated Leak Sites (DLS) grew 1.5 times compared to 2023. Despite this growth, the average number of unique posts per month has remained the same compared to the previous year.
Ransomware operators are also likely to continue to leverage leaked malware source codes and builders to create their own customized versions. This approach significantly lowers the barrier to entry for new groups, as they can avoid developing tools from scratch. The same goes for Dedicated Leak Sites (DLSs): low-skilled cybercriminals will likely use the leaked DLS source codes of notorious groups to create almost exact copies of their blogs – something we can already see happening on the dark web.

LockBit’s DLS

DarkVault’s DLS is almost an exact copy of LockBit’s
Escalating Cyberthreats in the Middle East: Rise of Hacktivism and Ransomware
According to Kaspersky Digital Footprint Intelligence (DFI), one of the most concerning cybersecurity threats related to dark web activity in the Middle East in the first half of 2024 was the activity of hacktivists. The region has seen an increase in these threats due to the current geopolitical situation, which is likely to continue to rise if tensions do not ease.
Kaspersky DFI researchers observed more than 11 hacktivist movements and various actors across the region. In line with the current geopolitical instability, hacktivist attacks are already shifting from distributed denial of service (DDoS) and website defacement to critical outcomes such as data leaks and the compromise of target organizations.
Another threat that is likely to remain highly active in the region is ransomware. Over the past two years, the Middle East has seen a surge in the number of ransomware attack victims, rising significantly from an average of 28 each six months in 2022-2023 to 45 in the first half of 2024. This trend is likely to persist into 2025.
Review of Last Year’s Predictions
Increase in Services Offering AV Evasion for Malware (Cryptors)
We continuously monitor underground markets for the emergence of new “cryptors,” which are tools specifically designed to obfuscate the code within malware samples. The primary purpose of these tools is to render the code undetectable by security software. In 2024, our expert observations indicate that commercial advertising for these cryptors have indeed gained momentum. Cryptor developers are introducing novel techniques to evade detection by security solutions, incorporating these advances into their malware offerings.
Pricing for these tools has remained consistent, ranging from $100 for a monthly subscription to cryptors available on dark web forums to as much as $20,000 for premium private subscriptions. There has been a shift toward the development and distribution of premium private solutions, which are becoming increasingly prevalent compared to public offerings.
Verdict: prediction fulfilled
Evolution of “Loader” Malware Services
As anticipated, the supply for the “loader” malware family has been constant in 2024. These loaders exhibit a wide range of capabilities, from mass-distributed loaders available at low prices to highly specialized loaders tailored to detailed specifications with prices reaching into the thousands of dollars.
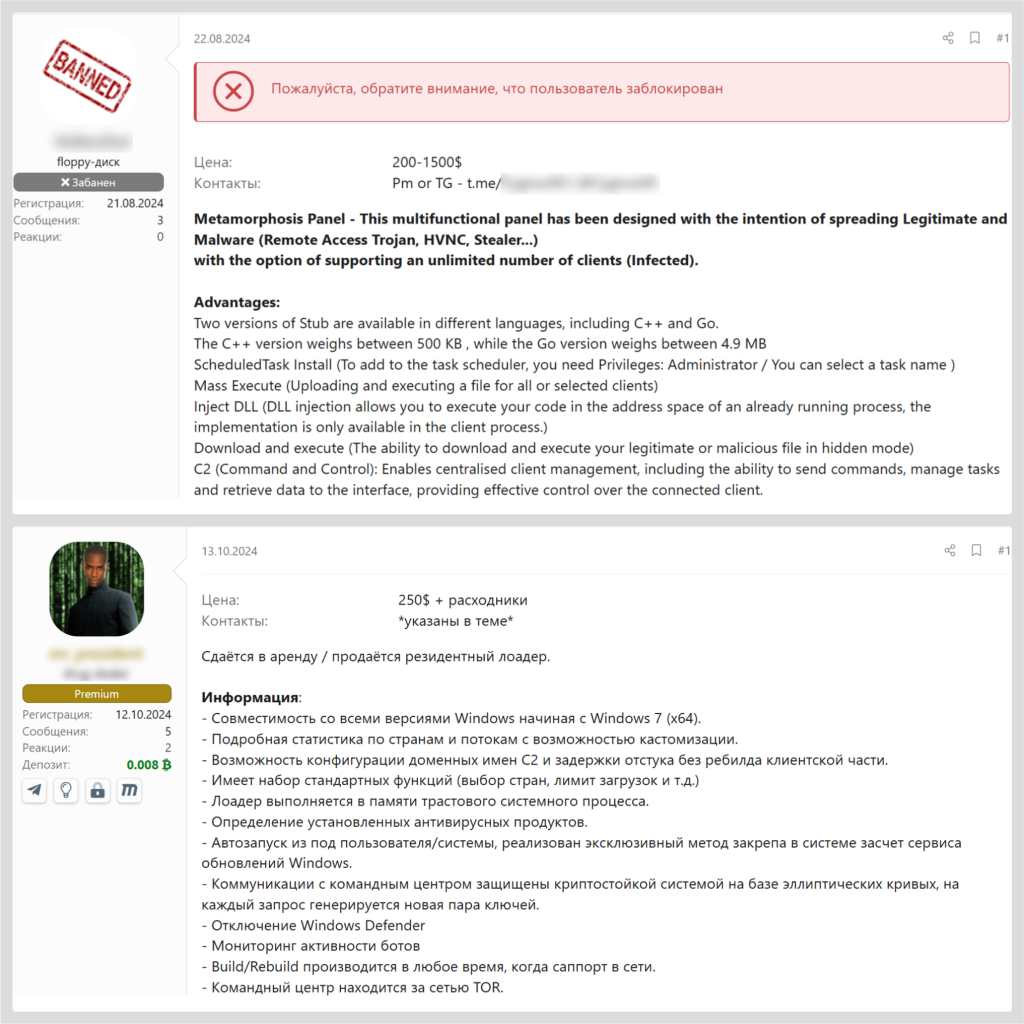
Examples of loader offers
Additionally, threat actors appear to be increasingly using multiple programming languages. For example, the client component of the malware may be developed in C++, while the server-side admin panel is implemented in Go.
Along with the wide variety of loader offerings, we have also seen demands for specific functionality tailored to launch a particular infection chain.
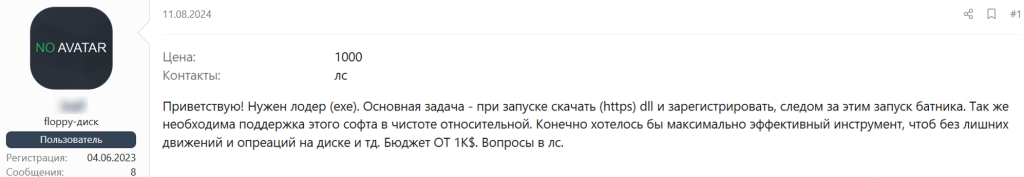
Example of searching for a loader with specific requirements
Verdict: prediction fulfilled
Growth of Crypto Asset Draining Services on Dark Web Markets
In 2024, we observed a surge in the activity of “drainers” across dark markets. These are malicious tools designed to steal the victim’s crypto assets, such as tokens or NFTs. New drainers emerged throughout the year and were actively promoted on various dark web platforms. In general, the number of unique threads discussing drainers on underground markets increased from 55 in 2022 to 129 in 2024, which is remarkable. At the same time, these posts frequently served as redirects to Telegram.
The number of unique threads about drainers on the dark web (download)
In fact, in 2024, Telegram channels were a prominent hub for drainer-related activity.
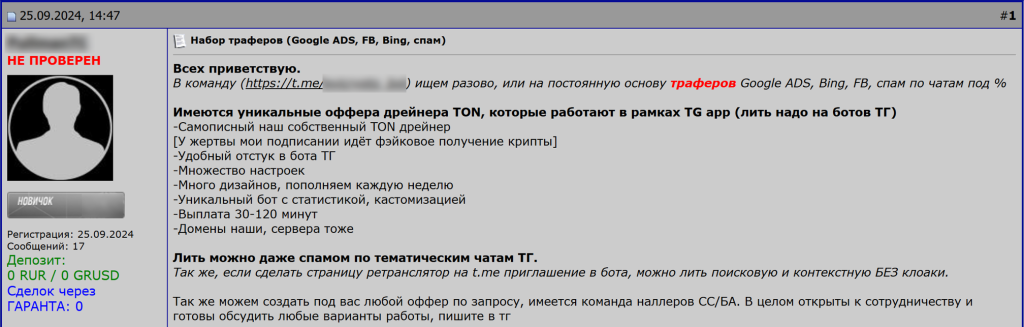
Dark web post containing links directing potential collaborators to Telegram
Drainer developers are increasingly focused on serving their long-term clients, with most activity now conducted in invite-only channels.
In terms of functionality, drainers have remained largely consistent, with a continued emphasis on incorporating support for new crypto-related assets such as emerging coins, tokens, and NFTs. 2024 also saw the discovery of the first mobile drainer.
Verdict: prediction fulfilled
Popularity of Black Traffic Schemes on Underground Markets
In 2024, the popularity of black traffic schemes on underground markets remained constant. Black traffic dealers have maintained their operations by promoting malicious landing pages through deceptive ads. Sales activities for these services remain robust on underground markets, with demand holding steady, further highlighting the effectiveness of mainstream ad delivery platforms for malware distribution. This method continues to be a popular choice for cybercriminals looking to reach a wider audience, posing an ongoing threat to online users.
Verdict: Partially fulfilled
Market Dynamics of Bitcoin Mixers and Cleaning Services
In 2024, there was no significant increase in the number of services advertising cryptocurrency “cleaning” solutions. The majority of established and popular services have maintained their presence in the market, with little change in the competitive landscape.
Verdict: prediction not fulfilled
Our Predictions for 2025
Data Breaches Through Contractors
When abusing company-contractor relationships (trusted relationship attacks), threat actors first infiltrate a supplier’s systems and then gain access to the target organization’s infrastructure or data. In some cases, these attacks result in significant data breaches, such as the case where attackers allegedly accessed Ticketmaster’s Snowflake cloud account by breaching a third-party contractor. Another prominent threat actor employing this tactic was IntelBroker – the actor and their associated gang reportedly breached companies like Nokia, Ford, a number of Cisco customers including Microsoft, and others through third parties.
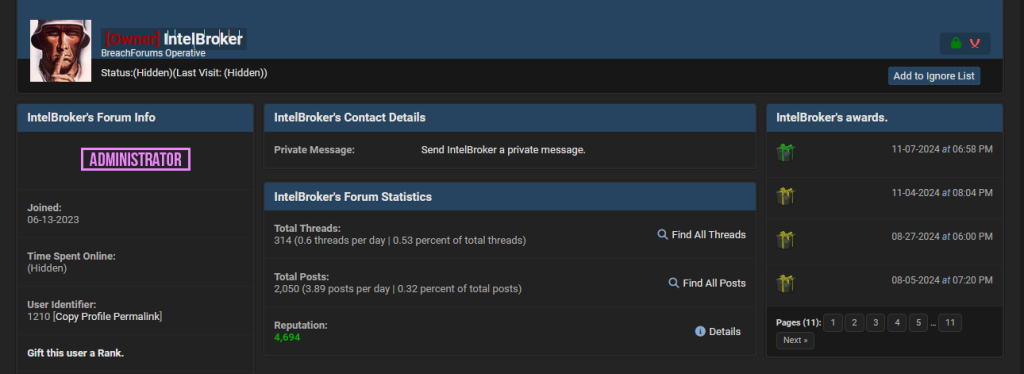
Profile of the actor named IntelBroker on a popular dark web forum
We expect to see the number of attacks through contractors leading to data breaches at major end targets to continue to grow in 2025. Cloud platforms and IT services often store and process corporate data from multiple organizations, so a breach at just one company can open the door to many others. It is worth noting that a breach does not necessarily have to affect critical assets to be destructive. Not every data breach advertisement on the dark web is the result of a genuinely serious incident. Some “offers” may simply be well-marketed material; for example, certain databases may combine publicly available or previously leaked data and present it as breaking news, or simply claim to be a breach for a well-known brand. By creating hype around what is actually old – and probably irrelevant – data, cybercriminals can provoke publicity, generate buzz, and damage the reputation of both the supplier and its customers.

IntelBroker’s dark web post claiming a Tesla data breach, later edited to claim to be a breach of a third-party EV charging firm
In general, we have noticed an overall increase in the frequency of corporate database advertisements on the dark web. For example, on one popular forum, the corresponding number of posts in August-November 2024 increased by 40% in comparison with the same period last year, and peaked several times.
Number of dark web posts distributing databases on one popular forum, August 2023-November 2024 (download)
While some of this growth may be attributed to the reposting or combining of older leaks, cybercriminals are clearly interested in distributing leaked data – whether new, old, or even fake. Consequently, in 2025, we are likely to witness not only a rise in company data hacks and leaks through contractors, but also an overall increase in data breaches.
Migration of Criminal Activity from Telegram to Dark Web Forums
Despite a spike in cybercriminal activity on Telegram in 2024, we expect the shadow community to migrate back to dark web forums. Shadow Telegram channels are increasingly being banned, as noted by their administrators:
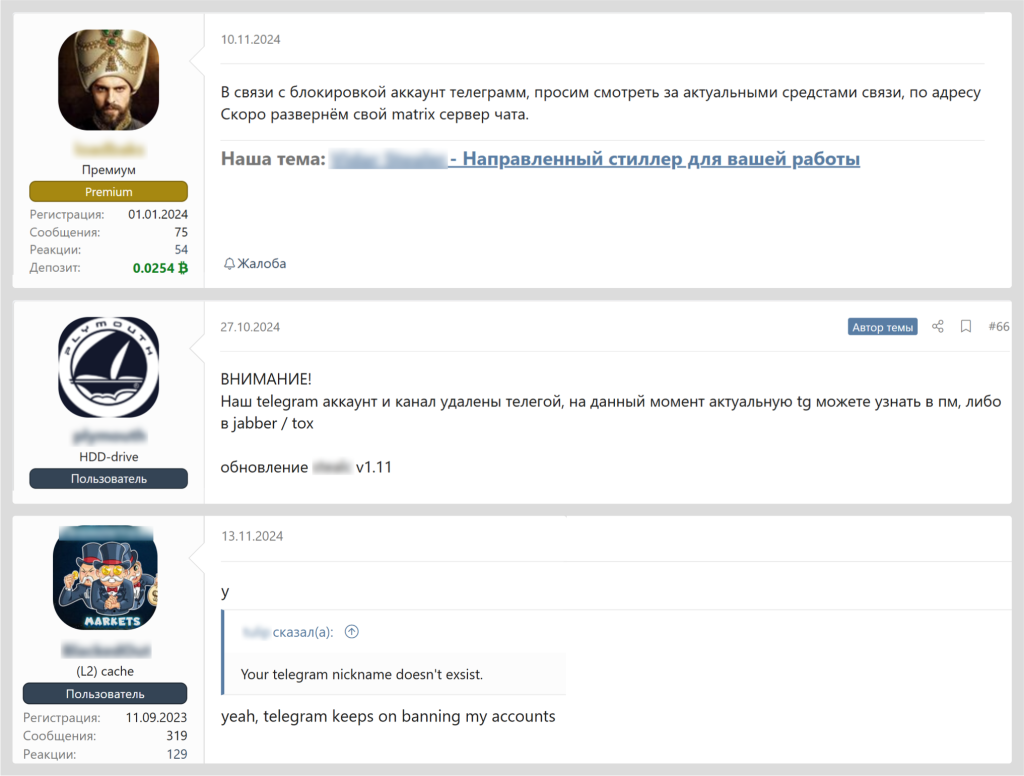
Examples of messages from threat actors announcing a ban on their Telegram channels and accounts
The return or influx of cybercriminals to dark web forums is expected to intensify competition among these resources. To stand out and attract new audiences, forum operators are likely to start introducing new features and improving conditions for data trading. These may include automated escrow services, streamlined dispute resolution processes, and improved security and anonymity measures.
Increase in High-Profile Law Enforcement Operations Against Cybercrime Groups
2024 was a significant year in the global high-profile fight against cybercrime. The world has seen many successful operations – Cronos against LockBit, the takedown of BreachForums, the arrest of WWH Club members, successful initiatives like Magnus against RedLine and Meta stealers, and Endgame against TrickBot, IcedID, and SmokeLoader, and more. We at Kaspersky also actively contributed to law enforcement efforts to combat cybercrime. For example, we supported INTERPOL-coordinated action to disrupt the Grandoreiro malware operation, helped counter cybercrime during the 2024 Olympics, and contributed to Operation Synergia II, which aimed to disrupt cyberthreats such as targeted phishing, ransomware, and infostealers. We also assisted the joint INTERPOL and AFRIPOL operation combating cybercrime across Africa. These and many other cases highlighted the coordination and collaboration between law enforcement and cybersecurity organizations.
We expect 2025 to bring an increase in arrests and takedowns of high-profile cybercriminal group infrastructures and forums. However, in response to the successful operations of 2024, threat actors will likely switch tactics and retreat to deeper, more anonymous layers of the dark web. We also expect to see the emergence of closed forums and an increase in invitation-only access models.
Rise of Stealers and Drainers as Services on the Dark Web
Cryptocurrencies have been a prime target for cybercriminals for years. They lure crypto users to scam sites and Telegram bots under various guises, and add crypto-stealing functionality to infostealers and banking Trojans. With the price of Bitcoin setting record after record, the popularity of drainers specifically designed to steal cryptocurrency tokens from victims’ wallets is likely to persist in the coming year.
Infostealers are another type of malware that harvests sensitive information from users’ devices, including private keys for cryptocurrency wallets, passwords, browser cookies, and autofill data. In recent years, we have witnessed a dramatic rise in credential leaks driven by this malware, and we expect this trend to continue – and in some sense evolve. Most likely, we will see the emergence of new families of stealers, along with an increase in the activity of those that already exist.
Both stealers and drainers are likely to be increasingly promoted as services on the dark web. Malware-as-a-Service (MaaS) – or “subscription” – is a dark web business model that involves leasing software to carry out cyberattacks. Typically, clients of such services are offered a personal account through which they can control the attack, as well as technical support. It lowers the initial threshold of expertise required by would-be cybercriminals.
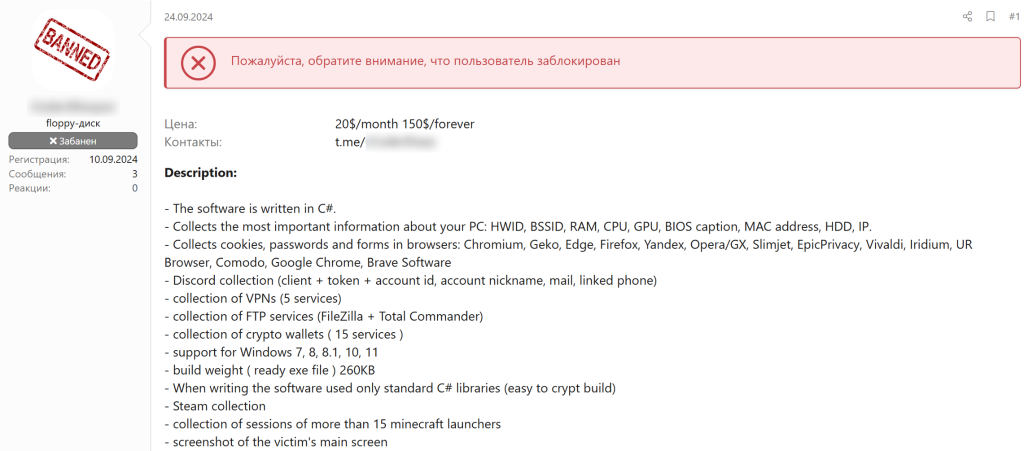
Example of a stealer offered through the MaaS model
In addition to publications on the dark web featuring stealers or drainers themselves, we also see posts looking for traffers – people who help cybercriminals distribute and promote stealers, drainers, or scam and phishing pages.
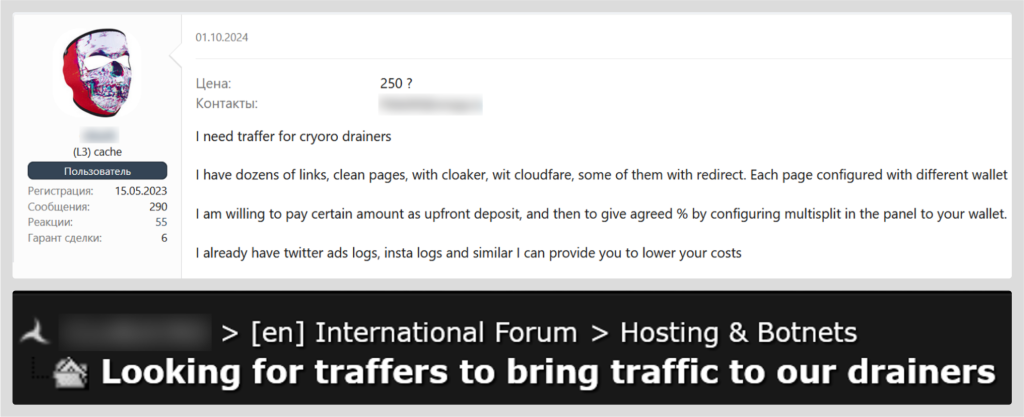
Examples of traffer searches for drainers
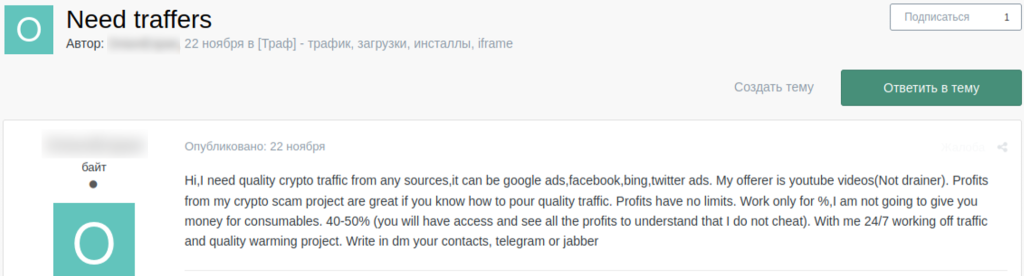
Example of a traffer search for a cryptoscam (not a drainer)
Fragmentation of Ransomware Groups
Next year, we may see ransomware groups fragmenting into smaller independent entities, making them more difficult to track and allowing cybercriminals to operate with greater flexibility while staying under the radar. Kaspersky Digital Footprint Intelligence data shows that in 2024 the number of Dedicated Leak Sites (DLS) grew 1.5 times compared to 2023. Despite this growth, the average number of unique posts per month has remained the same compared to the previous year.
Ransomware operators are also likely to continue to leverage leaked malware source codes and builders to create their own customized versions. This approach significantly lowers the barrier to entry for new groups, as they can avoid developing tools from scratch. The same goes for Dedicated Leak Sites (DLSs): low-skilled cybercriminals will likely use the leaked DLS source codes of notorious groups to create almost exact copies of their blogs – something we can already see happening on the dark web.
LockBit’s DLS
DarkVault’s DLS is almost an exact copy of LockBit’s
Escalating Cyberthreats in the Middle East: Rise of Hacktivism and Ransomware
According to Kaspersky Digital Footprint Intelligence (DFI), one of the most concerning cybersecurity threats related to dark web activity in the Middle East in the first half of 2024 was the activity of hacktivists. The region has seen an increase in these threats due to the current geopolitical situation, which is likely to continue to rise if tensions do not ease.
Kaspersky DFI researchers observed more than 11 hacktivist movements and various actors across the region. In line with the current geopolitical instability, hacktivist attacks are already shifting from distributed denial of service (DDoS) and website defacement to critical outcomes such as data leaks and the compromise of target organizations.
Another threat that is likely to remain highly active in the region is ransomware. Over the past two years, the Middle East has seen a surge in the number of ransomware attack victims, rising significantly from an average of 28 each six months in 2022-2023 to 45 in the first half of 2024. This trend is likely to persist into 2025.
Dark Web Trends: A Review of 2024 Predictions
As 2024 draws to a close, cybersecurity experts have revisited their predictions from last year, revealing a landscape increasingly dominated by sophisticated cybercriminal activities. Notably, the number of services offering AV evasion tools, known as cryptors, has surged. These tools, designed to obfuscate malware code, are now heavily advertised on underground markets, with prices ranging from $100 to $20,000 for premium subscriptions. This trend has been marked as a fulfilled prediction.
Loader malware services have also evolved, maintaining a steady supply of both mass-distributed and specialized loaders. The use of multiple programming languages in these services has become commonplace, enhancing their complexity and effectiveness. This prediction too has been confirmed.
The dark web has seen a dramatic rise in crypto asset draining services, with discussions about these malicious tools increasing from 55 threads in 2022 to 129 in 2024. Telegram has emerged as a central hub for these activities, facilitating a growing network of cybercriminals.
While black traffic schemes have remained popular, the prediction regarding the evolution of Bitcoin mixers and cleaning services did not materialize, indicating a stagnation in that sector.
Looking ahead, experts anticipate a rise in data breaches through contractor relationships, as threat actors exploit trusted connections to infiltrate organizations. The migration of criminal activities from Telegram back to dark web forums is also expected, driven by increasing bans on Telegram channels.
As cyber threats continue to escalate, particularly in regions like the Middle East, the landscape of cybercrime remains dynamic and ever-evolving. The predictions for 2025 suggest a continued focus on ransomware, hacktivism, and the proliferation of malware-as-a-service models, underscoring the urgent need for robust cybersecurity measures.





