The Emergence of The Gentlemen: A New Player in Ransomware
Introduction to The Gentlemen
In the third quarter of 2025, the cybersecurity landscape witnessed the emergence of a new ransomware group known as The Gentlemen. This group has made its mark by launching a specialized Data Leak Site (DLS) on the Tor network, showcasing a well-organized approach that sets it apart from other malicious entities.
Infrastructure and Operational Security
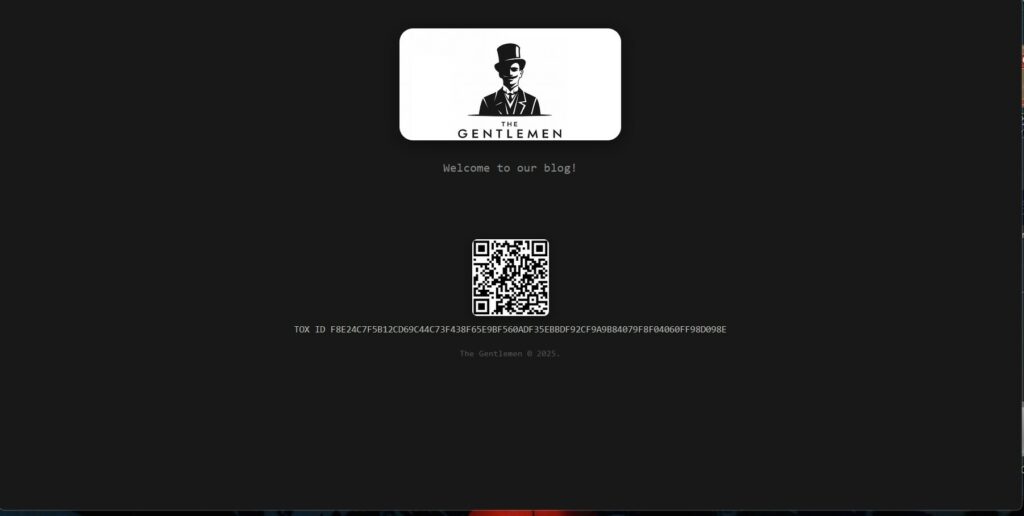
The infrastructure and operations of The Gentlemen reveal a medium to high level of sophistication. Their Data Leak Site, accessible via a unique .onion address, adheres to a minimalist design. This aesthetic not only provides a streamlined user experience but also enhances operational security. Key features of the site include:
- A minimalist homepage featuring a logo and clearly defined branding elements.
- Public availability of a TOX ID, suggesting a focus on encrypted peer-to-peer communications, likely to negotiate with victims.
- A redundant QR code facilitating easy contact access.
- A dedicated section for victims, organized with tabs that provide detailed descriptions of exfiltrated data.
By limiting unnecessary features and implementing decentralized protocols, The Gentlemen reduce potential vulnerabilities within their infrastructure.
Targeted Sectors and Victimology
The Gentlemen’s operations target industries with critical strategic importance, a tactic indicating a deliberate strategy aimed at entities with low tolerance for disruption and high reputational stakes. Identified sectors include:
- Manufacturing/Automotive in Europe
- Technology Services/IT Consulting in Asia
- Energy and Telecommunications on a global scale
This selection reflects an understanding of the economic and operational challenges these sectors face, making them prime targets for ransomware attacks.
Key Distinguishing Characteristics
What sets The Gentlemen apart from other ransomware groups? Several factors contribute to their unique identity:
- Strong Branding: Their consistent visual style aims to create a recognizable identity, distancing itself from more chaotic ransomware groups.
- Enhanced Operational Security: The group’s choice of TOX for communications indicates a preference for secure, decentralized methods over traditional centralized platforms.
- Modular Data Leak Site: The design of their DLS is scalable, indicating readiness to accommodate an increasing number of victim profiles and data disclosures.
These characteristics highlight a strategic approach that combines both technical proficiency and marketing acumen.
The Evolution of Ransomware
The introduction of The Gentlemen underscores the evolving nature of the ransomware landscape. This group showcases a meticulous attention to detail, exemplified by their well-structured DLS and targeted approach to selecting victims. It suggests that they are not merely a haphazard assembly of cybercriminals but rather an organized group possessing substantial resources and expertise.
The Implications for Businesses
For organizations, especially those in sectors vulnerable to such attacks, the rise of The Gentlemen serves as a crucial reminder. Enhancing network defenses and refining incident response strategies are no longer optional; they are an immediate necessity. As ransomware attacks grow in sophistication, businesses must remain vigilant and proactive in safeguarding their digital assets.
Conclusion
The Gentlemen’s entrance into the ransomware arena is a poignant reminder that cyber threats are continuously adapting. Businesses must take action to protect themselves, recognizing that the stakes are higher than ever in today’s interconnected world. By understanding the strategies employed by groups like The Gentlemen, organizations can better arm themselves against the potential fallout from cyberattacks.