Emergence of NtKiller: A New Threat in Cybersecurity
A sophisticated new tool known as “NtKiller” has recently emerged on underground cybercrime forums, introduced by a threat actor operating under the moniker “AlphaGhoul.” This tool is being marketed as a cutting-edge solution for stealthily dismantling antivirus (AV) and Endpoint Detection and Response (EDR) systems, providing ransomware operators and initial access brokers a potentially easier route to penetrate enterprise defenses.
Stealthy Attack Mechanisms
The advert for NtKiller, which surfaced on a well-known exploit forum earlier this week, positions the utility not merely as a process termination tool but as an advanced “defensive bypass enabler.” In the advertisement, AlphaGhoul asserts that NtKiller can effectively silence security products without triggering alerts, a feature that is highly coveted in the cybercriminal landscape.
What stands out about this offering is its purported compatibility with critical Windows security features such as Hypervisor-Protected Code Integrity (HVCI), Virtualization-based Security (VBS), and Memory Integrity. These features are designed to safeguard sensitive system processes, preventing the execution of harmful code at the kernel level. If AlphaGhoul’s claims are legitimate, it suggests that NtKiller may utilize advanced techniques, including Bring Your Own Vulnerable Driver (BYOVD) attacks, to gain heightened privileges and disable these protective measures directly.
Early-Boot Persistence
One of the more alarming claims made in the advertisement is that “targets are terminated at launch,” which implies that the tool is capable of executing early in the operating system’s boot sequence. This early-boot persistence mechanism could allow NtKiller to neutralize EDR sensors before they can fully activate, making the tool particularly effective at remaining undetected.
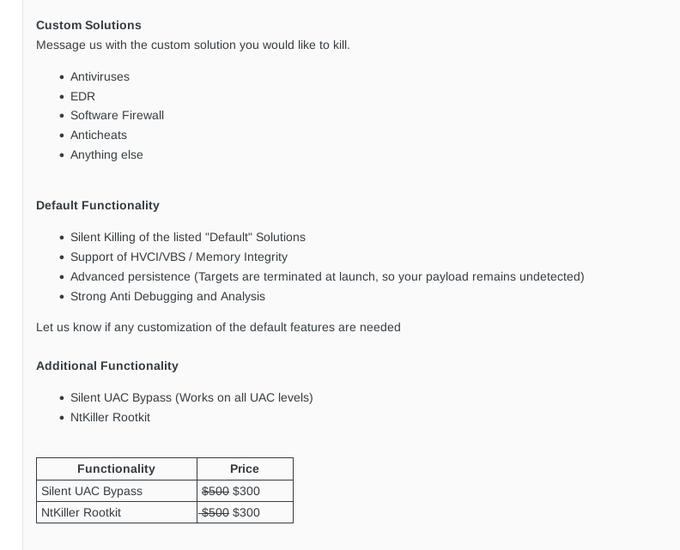
Pricing Structure and Features Available
NtKiller is offered with a modular pricing model, enabling users to tailor their attack capabilities according to their needs:
- Core NtKiller ($500): This base version allows for the silent termination of various mainstream security solutions including Microsoft Defender, ESET, Kaspersky, Bitdefender, and Trend Micro. It also provides support for VBS and HVCI environments, along with anti-debugging protections aimed at frustrating security researchers.
- NtKiller Rootkit ($300): This optional add-on appears designed to obscure the malware’s own processes, files, and registry keys, thereby ensuring long-term stealth from detection mechanisms.
- Silent UAC Bypass ($300): This feature facilitates the silent bypassing of User Account Control prompts, making it easier to escalate privileges without alerting the victim.
The total cost for the complete suite comes to $1,100, positioning it within the mid-to-high tier for such tools. This pricing suggests that the author is targeting serious criminal affiliates rather than casual users or “script kiddies.”
Potential Risks and Warnings
While AlphaGhoul’s assertions about NtKiller are concerning, it is important to note that these claims have yet to be independently verified by established security researchers. It isn’t unusual for sellers on these forums to embellish their offerings to enhance appeal and drive sales. Nevertheless, the specificity of the tool’s features—especially the claims related to bypassing VBS and Memory Integrity—warrants serious consideration from the cybersecurity community.
If NtKiller functions as described, tools of this nature could pose a significant risk to organizations that rely solely on endpoint agents for security. Security teams are encouraged to keep an eye out for indications of driver-based attacks, such as the installation of known vulnerable drivers or unexpected service terminations, which often occur prior to the deployment of advanced evasion tools like NtKiller.



